| |
| |
| Vulnerable Facebook Applications |
| Author:
Abhinav Singh |
| |
| |
| |
|
|
|
| |
| |
| |
|
|
| |
| |
|
Facebook has always been under the scanner because of its privacy
issues. Since its release in 2004, it has been target several times
because of its security measures. Over the course of time Facebook
did learn from its mistakes and improved its security measures on
how people share information on the platform. But an area where they
still don't have much control is the applications that are built
using the platform. Here is a statement from Facebook's privacy
policy about Third party applications,
|
"we do not own or operate the
applications or websites that use Facebook Platform. That means that
when you use those applications and websites you are making your
Facebook information available to someone other than Facebook"
|
| |
 |
|
|
This is where the users should be careful. Applications running on
Facebook cannot be trusted unless it belongs to a popular or trusted
app publisher. There are many such malicious and vulnerable
Facebook applications running on the platform which can misuse the
information that you share.
The main aim of this article is to make users aware of
vulnerable Facebook applications which attackers can take
advantage of and play with user's security.
|
|
|
|
|
|
|
|
|
|
We have received official note from Developer of "Name
Meaning" Facebook application that vulnerability mentioned
in this article has been fixed now. We thank author for bringing up
this issue and developers for quicking fixing this vulnerablity. |
|
|
|
|
|
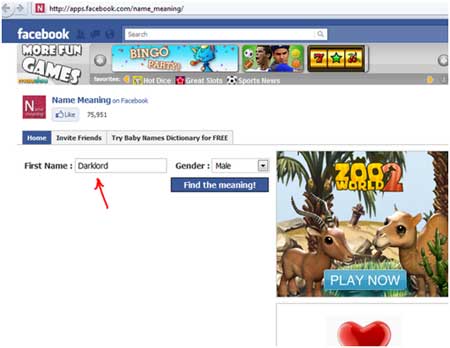
While performing some tests on Facebook
platform, I came across a vulnerable application 'Name Meaning'
[Reference 1] that can be attacked using Cross site scripting. This is an
interesting Facebook application which tells you the meaning of your name.
|
| |
 |
|
|
| As you can see that the application has
a text box where the user can enter his/her name to find out the
meaning. I went on to check this application with a normal reflected
XSS
attack by entering a small Javascript, |
| |
| <script>alert("HackingAlert")</script> |
| |
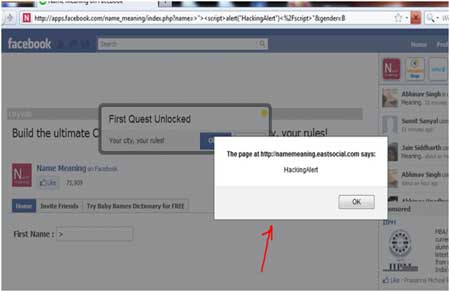
| This injection didn't work. So I went on to try my second dork with
a bit of advanced script injection to bypass the filter mechanism. Then
I little variant of the earlier javascript, |
| |
| >"><script>alert("HackingAlert")</script>" . |
| |
| This time the attack succeeded and an alert message
was generated showing the successful execution of the script as shown in
the screen below. |
| |
 |
| |
I further went on to check if I can insert more dangerous tags or
not. The next script that I crafted contained an <iframe> tag
to check
if my respective iframe gets displayed in place of the application or
not. The attack succeeded again and instead of displaying the
application in the iframe area, it displayed my blog url which I had
inserted in my script.
Here is my crafted script,
|
| |
| >"><script>alert("HackingAlert")</script><iframe
src="http://hackingalert.blogspot.com" width="400"
height="400"></iframe>" |
| |
Note, you will have to shift to HTTP version of Facebook instead of
HTTPS in order to use any of its third party applications.
|
| |
 |
| |
| Now any attacker can easily display a malicious link
(such as one shown below) in the iFrame
area and spread the URL. The attacker can use this technique to steal
cookies and perform session hijacking. |
| |
http://apps.facebook.com/name_meaning/index.php?name=++%3E%22%3E%3Cscript%3Ealert%28%22HackingAlert%22%29%3C%2Fscript%3E%3Ciframe+src%3D%22http%3A%2F%2Fhackingalert.blogspot.com%22+width%3D%22400%22+height%3D%22400%22%3E%3C%2Fiframe%3E%22&gender=B
|
| |
| Looking at this URL, user would believe that it belongs to the
Facebook application. In-fact it does belong to it but it has been
crafted to attack the user information. Vulnerability like this in
Facebook apps can easily be used to steal cookies of legitimate users
and lead to their security breach. |
| |
| |
| |
|
|
|
| |
|
This article shows how attacker can exploit vulnerable Facebook apps to
their advantage and play with innocent users.
Hence it is highly
recommended that you should not blindly trust any Facebook application.
Recently lot of spam and such vulnerable apps have flooded the platform
and Facebook does not take any responsibility for any information that
you share with third party applications within the platform.
So
THINK before you CLICK!
|
| |
| |
| |
|
|
|
| |
| |
| |
| |
| |
| |
| |